How to Sign Applications on Windows (SDK)
Let's take a look at signing an application on Windows using the Windows SDK (signtool tool) and a Code Signing certificate. This guide assumes you have a prepared Code Signing certificate in PFX format and the Windows SDK development environment installed on your Windows operating system. You can download the SDK from Microsoft's website for your respective Windows version, such as the Windows Software Development Kit (SDK) for Windows 10.
Using Signtool
Signtool.exe is a program that signs applications with a Code Signing certificate. After installing the Windows SDK, use it through the command line. To sign applications, you need to know the basic parameters so you can properly invoke the signing of an application with the correct certificate and settings.
The signing actually occurs through the command line, and the certificate only needs to be available on the given computer (it is not installed anywhere).
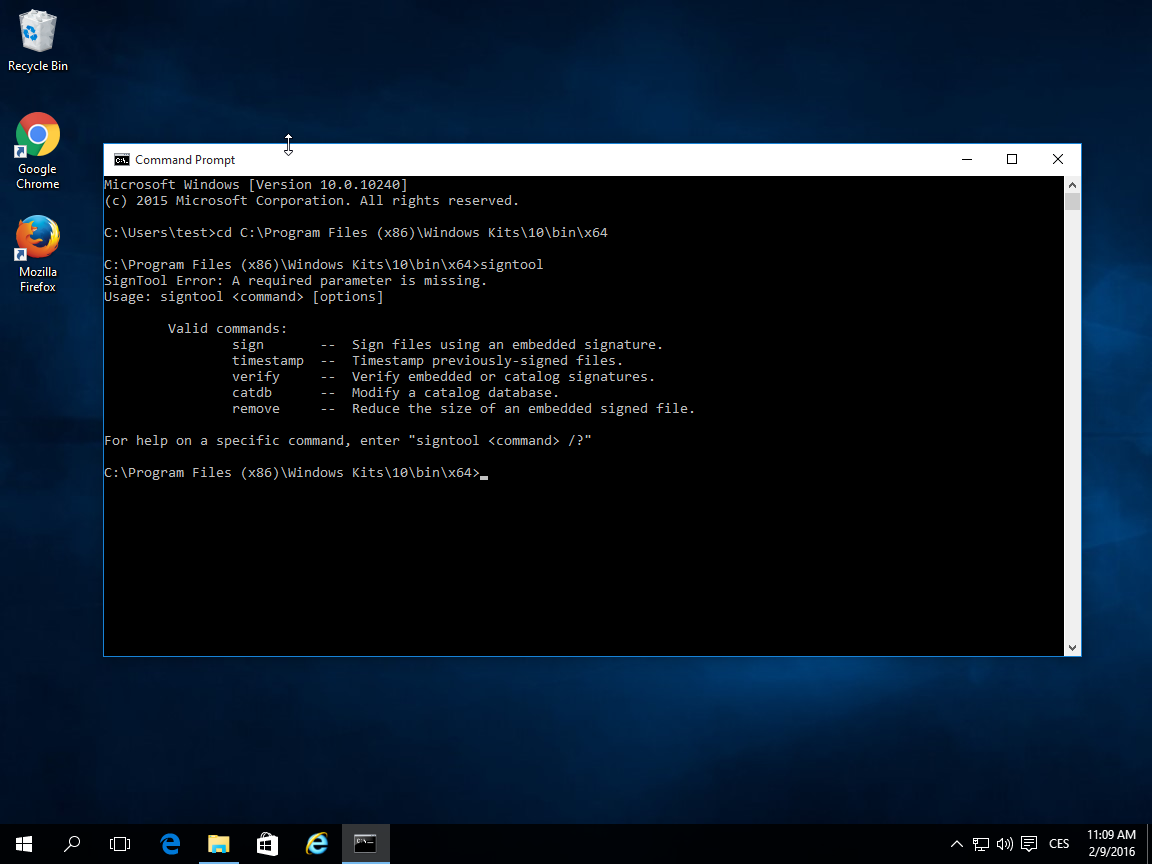
The basic parameters (commands) for signing are as follows:
signtool command /parameter
From the commands, you will use Sign to sign and Verify to verify the signature of a file. Timestamp is a command to insert a timestamp, but you can do this right during the signing of the file.
Useful parameters:
- /f SignCertFile – If using a PFX file for signing, this command refers to its location. Obtaining a Code Signing certificate in PFX is no longer possible.
- /s StoreName – If using a certificate store (e.g., on a token), specify which one to use. The default is My.
- /t URL – Adds a timestamp and a link to it. You can find the URL for timestamp servers below.
- /td - Digest algorithm for the timestamp. Choose at least sha256 or higher.
- /fd - Digest algorithm. Choose at least sha256 or higher.
You can find the complete documentation on the Microsoft website or by entering the command “signtool sign /?”.
The entire file signing command may then look like this:
SignTool sign /n "My Company Certificate" /td sha256 /fd sha256 /t http://timestamp.digicert.com C:\test.exe
Always use a timestamp. It ensures the signed application remains trustworthy even after the certificate's expiration, which was used for signing. This is very important because you won't have to re-sign older applications back (typically after two years when the Code Signing certificate expires) to prevent them from being untrusted. If you use a timestamp at the time of signing and the certificate is valid, the application will also be valid in the future.
There are many servers providing timestamps; I recommend using the DigiCert timestamp server: http://timestamp.digicert.com/
This server has no web page on port 80, so it is pointless to visit it with a browser (you will see nothing).
Certificate Stores
The certificate can be stored in multiple places (in several stores), and you can "invoke" it in several ways. Previously, it was possible to store the certificate as a PFX file, but this is no longer possible. A PFX file can be stolen by anyone, and although PFX is password-protected, it constitutes a major security risk (passwords often tend to be very weak). PFX is primarily suitable for backing up S/MIME certificates or for web usage.
The common way to store a Code signing certificate is to store it on a token and then call it according to the subject in the certificate. This method is secure and practically the same as past signing with PFX. Without the private key, which cannot be exported from the token, the certificate is useless and cannot be misused; if the password is entered incorrectly five times, the token will lock.
Signature using the store then requires a parameter /n SubjectName:
signtool sign /n "My Company Certificate" /td sha256 /fd sha256 /t http://timestamp.digicert.com C:\test.exe
Alternatively, you can choose the default store My, and the signing software will find the certificate automatically:
signtool sign /s My /td sha256 /fd sha256 /t http://timestamp.digicert.com C:\test.exe
Automating Code Signing with Cloud HSM
Automating code signing is highly demanded, but with a certificate on a token, it cannot be signed automatically; you cannot use it on a server either. Fortunately, there are services suitable for automating the signing process. DigiCert offers the service KeyLocker, or Software Trust Manager. You can also have your signing keys in a cloud HSM in Azure or Google Cloud.
More information on the possibilities of automating code signing can be found in the article Code Signing Center.
Verification of Signature
Now you know how to sign, and your application has its first trusted signature. You are surely interested now in how to check the signature.
Verification is possible using the signtool tool:
signtool verify C:\test.exe
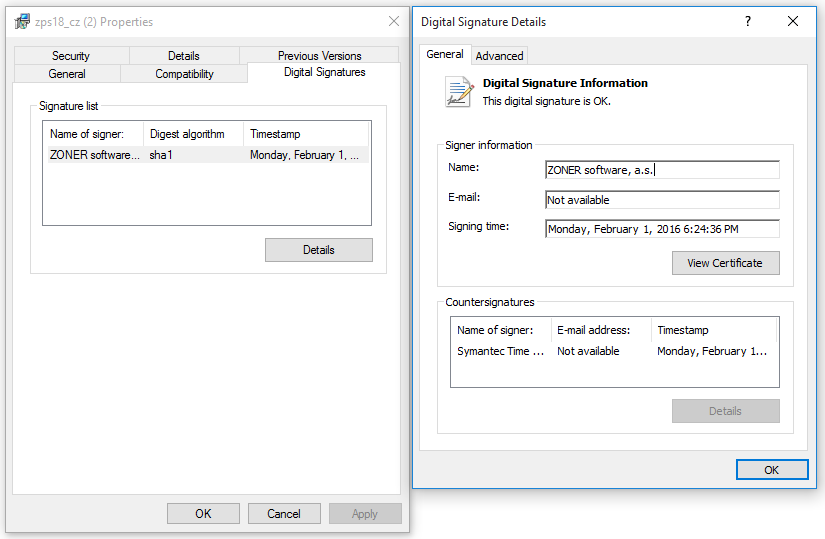
It is simpler to perform the verification by displaying the file properties in the Windows Explorer. You can "dissect" the signature detail down to the very details of the certificate used.

We are sorry that you did not find the required information here.
Please help us to improve this article. Write us what you have expected and not found out.